Drainer-as-a-Service in 2025: How Not to Hand Over All Your Crypto to a Scammer by Accident
Anyone can fall victim to a drainer.

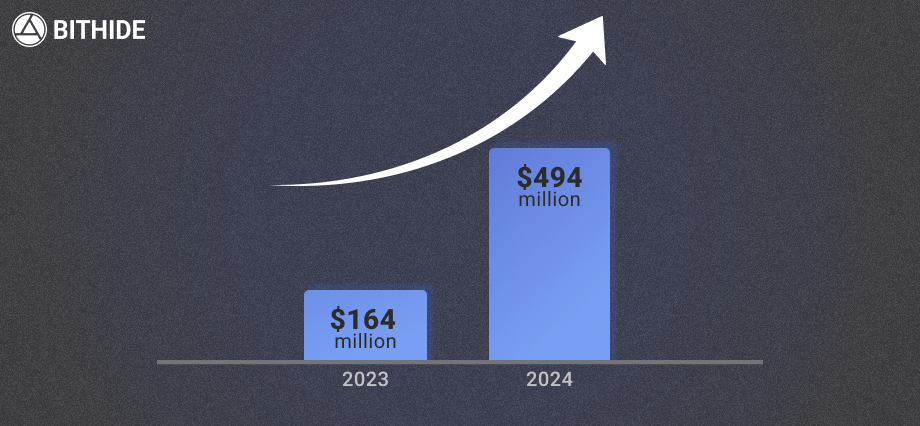
In 2024, drainers were used to steal over $494 million. This marks the rise of yet another cunning and deceptively simple scam in the crypto world. Victims range from complete newcomers to seasoned and wealthy crypto users — and the software behind it can be bought for just a small fee.
This article explains how drainers work, why they pose a particular threat to businesses, and how to protect your wallet and digital assets.
What Are Drainers?
A drainer is a malicious smart contract designed to completely empty a victim’s crypto wallet. These scams are mostly found in Web3, the decentralised web. Drainers are increasingly being distributed as ready-made software (drainware). However, rather than targeting the breach of endpoint security, they rely on social engineering — the user themselves confirms the transactions, believing they are interacting with a legitimate interface. Drainer-as-a-Service refers to “drainer-for-hire” operations.
Before we go any further, here are a couple of terms you’ll see throughout the article:
- NFT — a non-fungible token proving digital ownership of something online, such as an image, music, or even a ticket to an event.
- Smart contract — a blockchain-based program that automatically executes actions when certain conditions are met. It runs exactly as written, without human intervention, and can't be altered once deployed.
How Do Drainers Work, and Where Are They Found?
According to Scam Sniffer, $494 million was stolen via drainers in 2024 — a 67% increase from 2023, when $164 million was taken using this method. Researchers examined the 30 largest drainers-based thefts in 2024. Of these, 25 (85.3%) occurred on the Ethereum network. This is no coincidence:
- Ethereum has high liquidity and asset value, making it a prime target for scammers.
- Most Web3 sites and NFT projects are built on Ethereum or compatible chains.
- Ethereum's reputation for security gives users a false sense of safety — they’re often too relaxed when approving transactions.
The remaining major thefts took place on other chains: two on Arbitrum, and one each on BNB Chain, Base, and Blast.
How a Drainer Works
Contrary to popular belief, a crypto drainer doesn't gain control over the user’s private keys. Instead, the malicious smart contract tricks the user into granting it permission to move assets — all without them realising it.
Here’s how it typically works:
- A user comes across a phishing dApp (decentralised app) disguised as a well-known platform (like Uniswap or OpenSea), a fake token giveaway (airdrop), an NFT marketplace, or a GameFi project.
- While interacting with the site, the user is prompted to confirm a transaction in their wallet (such as MetaMask or Trust Wallet) — supposedly to mint an NFT or claim an airdrop. In reality, this authorises the smart contract (via approve, setApprovalForAll, or permit) to control the user's tokens or NFTs.
- The scammer’s bot instantly detects the approval and drains the wallet within seconds.
Here’s a breakdown of how permission is granted:
- “approve” — A standard ERC-20 function that lets a trusted smart contract manage tokens on the user’s behalf.
- “setApprovalForAll” — The equivalent for NFTs (ERC-721 and ERC-1155).
- “permit” — Grants token access via digital signature instead of a transaction, avoiding gas fees. Commonly exploited in drainers targeting airdrop hunters.
These three functions are at the heart of the entire Wallet Drainer scam model.
The Drainer-as-a-Service (DaaS) Model
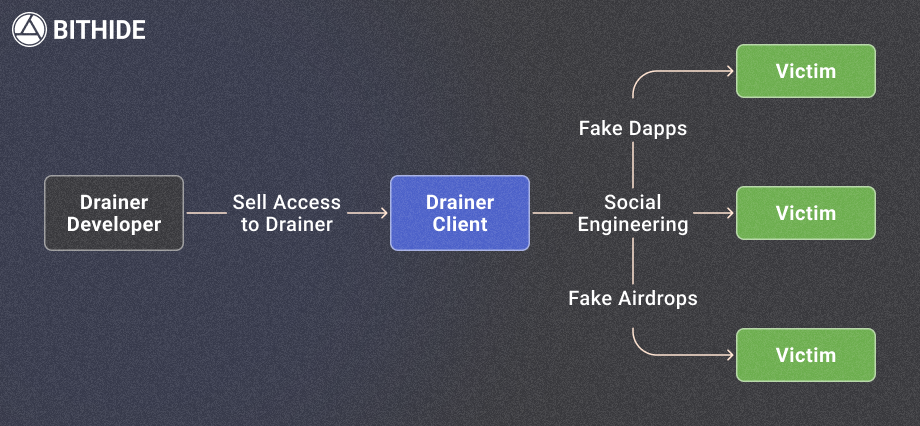
This term refers to a malicious business model where developers sell ready-made kits to steal crypto using smart contracts. The real danger? Anyone can purchase these kits for a relatively low price — around $100 to $300. The package typically includes:
- the crypto drainer software with a user-friendly control panel
- a rented domain
- tools to obscure online activity
- documents for passing KYC checks
- hacked or freshly created Telegram, Discord, and X accounts.
Why DaaS Is Becoming a Widespread Threat to Businesses
Previously, crypto theft required technical skills. Now, it just takes $300. DaaS turns asset theft into a plug-and-play business.
Businesses are especially vulnerable — they handle large transaction volumes, often have publicly visible wallet addresses, and employ many people. The more staff, the greater the risk that someone will mistakenly grant access to a malicious smart-contract.
Crypto Wallet Security: The BitHide Case
A business owner who accepted crypto payments approached us with a request: “We need a secure wallet that allows multi-user access for staff, but also includes advanced protection against hacks and drainers.”
Unfortunately, the company had previously suffered a loss due to an employee accessing a phishing site using the corporate wallet. The malicious contract was authorised, and all funds were instantly stolen.
BitHide offers multi-layered protection for both assets and data, even if someone within the company accesses Web3 sites without proper DeFi security awareness.
Untraceable Wallet Activity

Hackers tend to target wallets holding valuable NFTs or handling large sums. Our goal at BitHide is to conceal client business activity from bad actors. Here's how we do it:
Real IP Address Protection
The wallet changes its address multiple times for each transaction, making it nearly impossible to determine the true one — and preventing IP-based transaction linking.
Gas Stations
BitHide uses separate addresses to pay gas fees on Tron, BNB, and Ethereum. When a preset limit is reached, the address is rotated. This makes tracking the wallet much harder and prevents de-anonymisation or clustering.
Proxy Payments
Businesses often have a central wallet address for collecting funds. These are easy to track. BitHide eliminates this risk by using proxy payments — one-time intermediary addresses that can't be linked or clustered.
Sub-Wallets
You can create unlimited sub-wallets. Incoming funds from different revenue streams are routed to wallets that are not connected to one another. So even if one wallet is compromised, the others remain safe.
Role-Based Access Control
BitHide allows you to assign different roles and permissions to staff members based on their responsibilities.
This is just a fraction of what BitHide offers. If you want to learn more about how it can protect your business, get in touch to book a product demo.
Wallet Drainer Protection: Key Tips
To ensure you don’t add your funds to the growing total lost to malicious smart contracts, follow these best practices:
- Use a fresh, empty wallet for interacting with Web3 projects, airdrops, or NFT mints.
- Never connect your wallet to unknown sites, and double-check even familiar URLs. Phishing domains often look deceptively similar (e.g., uniswap․com → unlswap․com).
- Never click "Sign" or "Confirm" if you're unsure why the site is asking.
- Use tools like Revoke.cash or Etherscan Token Approvals to check and revoke existing permissions.
- Be sceptical of messages about airdrops or NFT mints, especially in Discord, Telegram, or X — they’re often drainer bait.
Conclusion
As the crypto world evolves, so do the scams that target it. Staying informed about new threats — like Drainers — and how to prevent crypto scams is essential to safeguarding your assets.
We hope this article has helped you understand how drainers work. If you're looking for secure, private, and convenient crypto payment solutions, get in touch — our team will be happy to show how BitHide can support your business.
— The BitHide Team


