Analysis of the Nova Trading Hack: How Convenience Became a Vulnerability
Telegram bots and security: lessons from the Nova Trading hack.

Crypto users often consider speed and convenience the main characteristics of asset management tools, forgetting about security. This carelessness can result in losses of hundreds of thousands of dollars. On September 16, 2025, a trader lost more than $576,000 in just a few hours due to centralized storage of private keys and a weak security system in the Nova Trading Platform, a Solana-based bot.
In this article, we will examine what happened, which mistakes were critical, and what lessons traders and companies can learn to protect their crypto assets from similar risks.
Key Takeways
- Nova Trading Platform is a Telegram bot for trading on Solana that executes transactions on behalf of users, supports automation, copy trading, and managing multiple connected wallets simultaneously.
- Users’ private keys are stored centrally on Nova’s servers, creating a single point of failure: any server leak or hack immediately jeopardizes all connected wallets.
- On the night of September 16, 2025, the trader’s wallet was drained of cryptocurrency worth ~$576,000. The victim publicly documented the incident on X, stating that the funds were withdrawn through a series of large transactions in a short period.
- $200,000 of the wallet remained untouched, indicating a targeted attack rather than a random theft, with a partial focus on specific assets.
- The stolen funds were routed through legitimate DeFi protocols, including token aggregators and liquidity pools, which significantly complicated tracking and recovery efforts.
- The incident revealed a structural risk of the platform: ease of use via a Telegram bot and automation came at the expense of basic security.
- Practical security recommendations for traders and teams.
What is the Nova Trading Platform
Nova Trading Platform is a trading bot built on Solana that operates entirely through Telegram. It provides users with fast and convenient access to crypto trading through the following features and tools:
- Support for up to 10 simultaneously connected wallets.
- Automation modules (Ultra V2 and Demon) based on the Jito block engine for high-speed transactions and MEV protection.
- Real-time copy trading, replicating the strategies of “whales.”
- Built-in risk management with automatic take-profit and stop-loss settings.
- Fee structure: 1% per transaction + gas.
- Referral program: up to 30% of direct referral fees.
- Nova Click (Chrome extension): adds trading buttons directly on DEX platforms such as BullX and Photon.
In practice, Nova acts as an intermediary, executing transactions on behalf of users through Telegram, making trade management extremely simple but creating risks for asset security.
Incident Facts
The affected trader, with the nickname Cupseyy (@Cupseyy), publicly documented the incident on X. At the time of the hack, his wallet was connected to only four platforms:
- Jupiter (DEX on Solana).
- Axiom (trading platform).
- Photon (trading bot).
- Nova (trading bot).
The trader ruled out the possibility of a browser-based attack, as he simply did not use extensions. According to him, this was a manual “drain” — deliberate actions by a person rather than scripts. This is evidenced by the untouched $200,000 left in the wallet.
The attack began on September 16, 2025, at 11:21 UTC. Funds were withdrawn in large transactions within a narrow time window and distributed across multiple addresses. Here is a detailed breakdown of the user’s losses by blockchain and transaction.
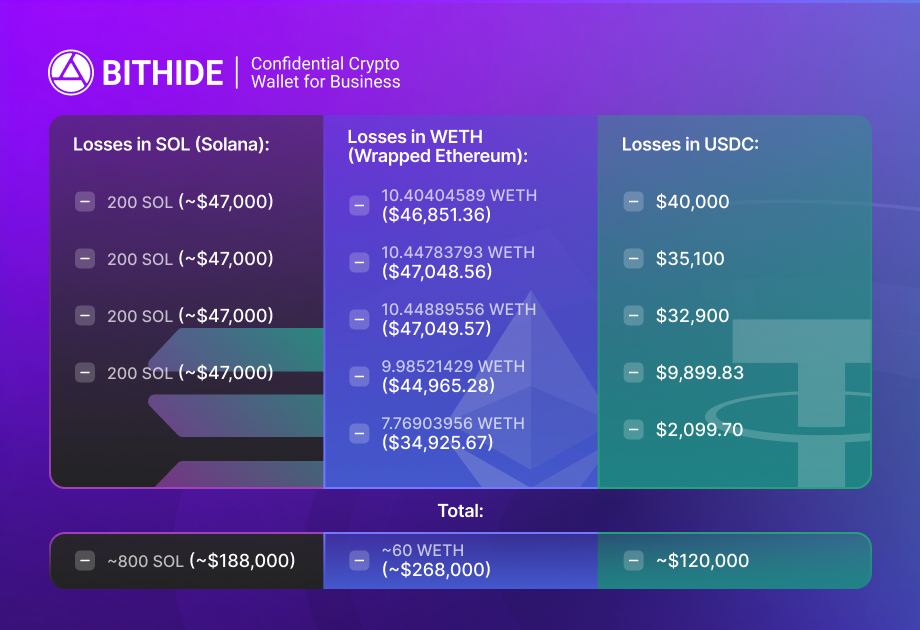
Total confirmed losses (conservative estimate): $576,000+. The stolen assets were routed through legitimate DeFi protocols, complicating tracking and recovery:
- Jupiter Aggregator for token swaps.
- Jupiter Labs Perpetuals for derivatives trades.
- Phoenix liquidity pools for additional obfuscation.
Hack — a Result of Structural Issues
The theft was possible due to the platform’s architecture. Its developers prioritized convenience and speed over basic security.
Centralized Private Key Storage
For trade automation, Nova stores users’ private keys on its servers. This creates a single point of failure: a server hack or insider attack immediately puts all connected wallets at risk.
Expanded Attack Surface via Integrations
The Nova ecosystem includes Nova Click (Chrome) and integrations with other tools such as Axiom Pro, which require synchronization of private keys across services, significantly increasing risk.
Complaints Preceded the Attack
Throughout September 2025, several users reported security issues with Nova. Some even suspected the involvement of a dishonest developer, although there is no proof or public confirmation. Altogether, these complaints point to a systemic flaw that could have affected dozens of users who entrusted their private keys to the platform.
Risk Model Analysis: When UX Convenience Contradicts Basic Security
Telegram bots are fast, simple, and attractive to traders, but most sacrifice fundamental ownership principles for convenience:
- Private keys are stored in the cloud.
- Transaction signing depends on centralized APIs.
- Source code and infrastructure are closed and opaque.
This means even a small configuration error or leak can instantly deprive a user of their assets. The industry principle: “Not your keys — not your coins” is not a cliché but the foundation of crypto security. Once a third party controls your keys, you lose control of your funds.
Practical Recommendations for Traders and Teams
If you use Telegram trading bots, these security rules are essential:
- Never store significant amounts in bot wallets — only keep the working balance needed for trading.
- Regularly withdraw profits to cold wallets that you fully control.
- Check which asset protection measures the platform provides before depositing.
- Study past incidents and user reports — ignore marketing and rely on evidence.
- Prefer decentralized exchanges where you hold the keys. If using intermediaries, keep only minimal working balances with them.
- Audit access rights and integrations of all connected apps. Set up notifications for unusual activity or unauthorized access.
Conclusion
The Nova Trading story shows that even the most advanced tools lose their value if basic security rules are ignored. Control over private keys remains the only reliable way to preserve assets.
If a platform asks for your private key, it is asking for your funds. In DeFi, this is a compromise that no serious trader or business should accept. No one except you should have access to your private keys. Contact our team to learn which technologies ensure the security of BitHide clients’ assets.


