Cryptocurrency Tracking: from Wallet to Real Identity
From IP address to Instagram post: how your transactions can be tracked and linked to you.

Blockchain technology is not an anonymous network, it’s a transparent ledger. It doesn’t include names, but it does contain everything needed to uncover identities: wallet addresses, transaction details, activity timestamps, and most importantly, IP addresses.
This data is collected and stored by nodes, some of which are controlled by criminals and hackers. They link crypto wallets to real people and can even determine their physical location.
In this article, we explain how transaction deanonymization works and why it can be dangerous for cryptocurrency users.
How Cryptocurrency and Businesses Are Tracked
Companies process far more transactions than individual users, making it easier to de-anonymize their activity and calculate transaction volume. Here’s how your transactions in the blockchain can be tracked and tied to your identity:
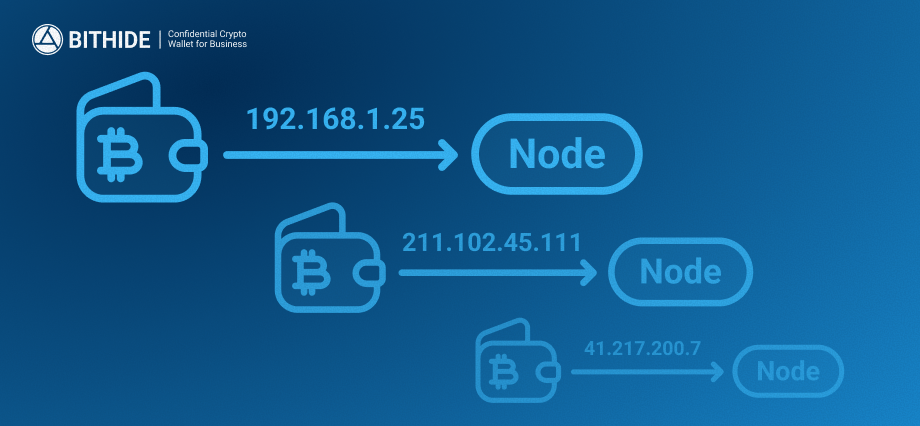
1. IP Address and Network Metadata Tracking
Every time a transaction is made, the wallet connects to a public node and sends its real IP address along with metadata such as timestamps, device type, and other technical details. Many nodes are owned by hackers and cybercriminals. Once they log your real IP address, they can link it to your wallet and start tracing every transaction you’ve made.That’s how they can track your wallet and your physical location.
Such cases have already led to violence and extortion. Dozens of crypto investors and entrepreneurs have been kidnapped around the world. One of the most well-known incidents is the recent abduction of David Ballan, co-founder of Ledger. He was eventually rescued, but not before the attackers cut off his finger.
2. On-Chain Labels and Tagged Address Databases
On-chain labels are tags applied to blockchain addresses. For example, if an address is linked to a mixer or darknet market, analytics platforms (Chainalysis, Elliptic, TRM Labs) flag it as “suspicious.” All cryptocurrency that passes through it inherits a high AML risk level. This information is permanently recorded in the blockchain. Even if the funds were mixed or routed through intermediate wallets, they remain “tainted.”
Businesses interacting with such cryptocurrency are placed in high-risk zones. In another article, we described how a company had its assets frozen due to a single suspicious payment from a client.
3. Off-Chain Analysis: Telegram, GitHub, Social Media
Off-chain source analysis (outside the blockchain) is becoming increasingly common. Project owners and business wallet users often reveal critical details themselves: ENS names, wallet addresses on landing pages, forum comments, Telegram chats, GitHub repositories, Twitter/X, Discord, and API documentation. Public information often allows wallets to be directly linked to a company, developer, or project.
For example, in December 2024, Ukrainian Ihor Yermakov and his driver were kidnapped in Bali and forced to transfer approximately $214 000 in crypto from a Binance account. The attackers may have identified the victim through a combination of off-chain signals (Telegram posts, Instagram activity) and on-chain data.
A year earlier, also in Bali, crypto investor Yurii Boitsov was robbed. Four intruders broke into his villa and forced him to transfer $284 000 in bitcoin to their wallet. It’s likely they identified his location through his social media posts.
4. Graph Analysis, Entry and Exit Points
Attackers build graph chains of crypto transfers — from the client to a payment gateway, then to distribution and final wallets. Even if many intermediate addresses are used, links between them can be restored using analysis of timing, volume, and transaction structure. These graphs visualize the movement of funds and reveal business logic.
Even if a company's workflow is entirely on-chain, exits to centralized exchanges (CEXs) remain a weak point. Any crypto deposit or withdrawal on an exchange leaves a trace in the blockchain that can be matched to a KYC-verified profile. These records stay in the blockchain forever and become part of the on-chain trail, which can ultimately lead to the real wallet owner.
5. Behavioural Profiling and Pattern Analysis
Machine learning analyzes how users interact with the blockchain. It considers parameters like wallet login frequency, time between transactions, response speed to events (e.g., price movements), and transaction volumes.
An example: mass payouts on specific days each month or repeating amounts typical of salary payments. Such patterns can distinguish individual users from organized businesses.
6. Vulnerable Points in Callbacks and APIs
Many businesses use callback notifications and open APIs to receive transaction statuses or automate crypto payments. But without proper protection, such as data signing and encryption, callbacks are vulnerable. They can be intercepted or analyzed to reveal transaction flows, wallet addresses, and business logic: who is paying, how much, and to whom.
For example, one iGaming platform was attacked when hackers compromized its callback data. They faked account balance info and withdrew funds from player accounts that didn’t actually have money. After the incident, the company contacted us to secure their infrastructure.
BitHide uses encrypted callback notifications to prevent tampering or interception. Each notification includes a cryptographic signature, allowing clients to verify the authenticity of the event.
Conclusion
There are many ways to link a crypto wallet to a real-world identity. Deanonymization can lead, at best, to major financial losses and, at worst, to violence or bodily harm. Be cautious: do not share that you own cryptocurrency on social media, and avoid opening wallets or portfolios in public places. For businesses working with crypto, it is essential to choose secure payment solutions designed specifically for companies. Contact our team to learn how BitHide can address your business needs.


