BitHide Transaction Safety Levels: a New Standard of Privacy on the Blockchain
Control the privacy level of your business transactions.

Blockchain was originally designed as a transparent system, and all transactions remain publicly accessible forever. In practice, this means that any observer can track a company’s financial flows, identify key counterparties, merge all addresses into a single cluster, and even determine real-world business owners.
Unlike the banking system, where transaction data is protected by law, on the blockchain you are essentially working in a “glass house.” If your funds are in a public network, you are visible. The only question is who is watching: a competitor, a partner, an analyst, or a malicious actor. For businesses, the situation becomes even more complicated because standard anonymization tools are not suitable:
- mixers carry legal risks and regulatory uncertainty. Many of these services are under sanctions, so any funds associated with mixers can be frozen at any moment;
- privacy coins are inconvenient for regular payments, as they lack mature infrastructure for corporate use. Moreover, transactions with Monero, Zcash, and similar assets are considered suspicious by default, which complicates cooperation with payment gateways.
This article explains BitHide’s Transaction Safety Levels, the first technology that provides privacy control at the level of each transaction while maintaining full AML compliance.
Key Takeaways
- Blockchain is transparent, and standard privacy tools do not work for businesses.
- Hackers and fraudsters can trace blockchain transactions and link a wallet to a real identity. On-chain and off-chain data, graph analysis, and more all help them.
- BitHide Transaction Safety Levels are the only business-oriented tool on the market that ensures managed confidentiality and compliance with regulatory requirements.
- Companies need predictable and regulated privacy — not absolute anonymity, but control over the level of data exposure.
How Are Blockchain Addresses “Linked” to Individuals?
Combining On-Chain Data with External Sources
Analysts collect not only addresses and amounts but also behavioral data: the time and frequency of transactions, recurring routes, and the balance of incoming and outgoing funds. These patterns are correlated with KYC data from exchanges and swap services. It takes just one address to complete verification for the entire connected chain to receive an ownership label tied to a specific individual or company.
If network traffic at an organization’s perimeter is monitored while the blockchain is simultaneously observed, timing correlations allow a pseudonymous address to be linked to a real source. Such an attack requires almost no resources and works effectively in networks such as Ethereum, Bitcoin, and Solana. A combination of a network “fingerprint” and public transactions almost always makes it possible to identify the source of a transfer.
Working with Network Metadata

When a crypto wallet connects to a blockchain (through an RPC node or a browser provider), network metadata is recorded: IP address, request time, device information. This data can be correlated with transaction logs, and an ordinary crypto wallet can turn into an open window into a company’s infrastructure.
Even popular wallets such as MetaMask and Trust Wallet send requests through Infura/Alchemy by default, and these services log IP addresses for every transaction. A user often does not even realize that by paying for something in cryptocurrency, they are revealing their geographical location to the provider, which can be inferred from the IP address. Later, this information may fall into someone else’s hands. Even if a company creates a new wallet address for every transaction, the digital footprint still remains.
At the moment, there is only one technology that allows the real IP address and address metadata to be successfully hidden without the risk of blocking or data leaks — Dark Wing by BitHide.
Graph Analysis: How Address Ownership Is Identified
At the level of blockchain data, algorithms for graph analysis are applied. All addresses and transactions form a network of nodes and edges, where nodes represent addresses and edges represent transfers. Analytical platforms construct this graph and attempt to simplify it, for example, by grouping addresses belonging to a single wallet or identifying “centers” of activity. Graph Neural Networks are capable of learning from the structure of such a graph and identifying clusters according to hidden indicators.
For businesses, this means that internal financial relationships become visible from the outside: an analyst can infer which address represents your revenue from sales, which ones correspond to payments to contractors, and so on.
OSINT and Social Engineering
When technical analysis alone is insufficient, social engineering and OSINT (open-source intelligence) are used. Professional analysts track companies’ public statements: partnership press releases, funding round announcements, job postings, social media posts, and so on.
As a result, the combination of technical signals and OSINT makes it possible to reconstruct a company’s financial model: to see turnover, key counterparties, internal payments, investment steps, and even indirectly determine strategic plans. For an external observer, a company “on the blockchain” can become almost transparent.
BitHide Transaction Safety Levels
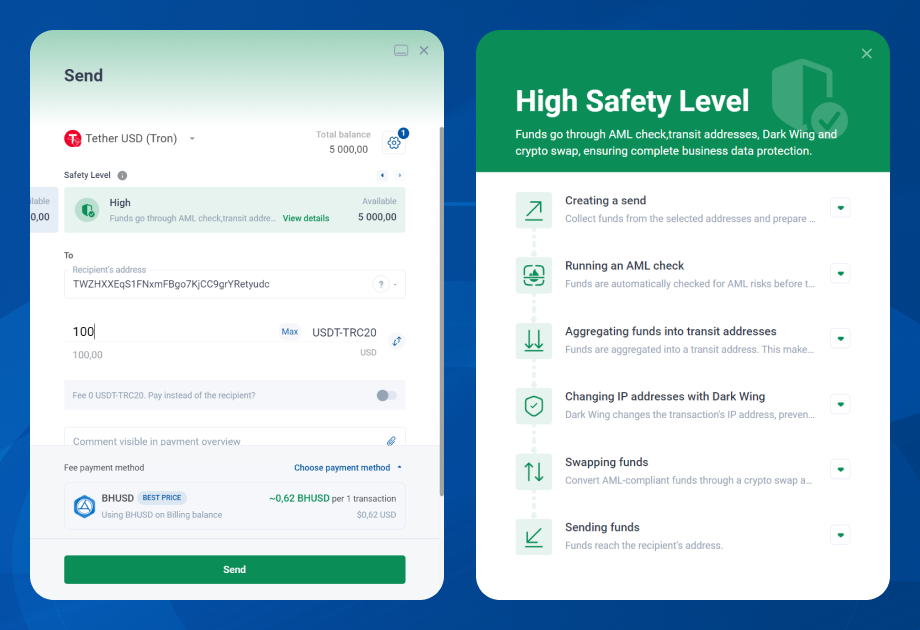
The BitHide tool solves the problem of full blockchain transparency and the exposure of sensitive company data. Businesses gain privacy control at the level of each transaction while maintaining full AML compliance:
- Basic Safety Level — the wallet’s real IP address is changed using the unique Dark Wing technology. This protects infrastructure and prevents metadata leaks.
- Medium Safety Level — enhanced protection: IP addresses are hidden via Dark Wing combined with fund aggregation at a transit address. This prevents observers from tracking the structure of a company’s financial flows or its operational patterns, strengthening overall privacy.
- High Safety Level — the IP address is changed multiple times via Dark Wing, then funds are aggregated at a transit address, undergo AML screening and safe conversion, and only then are sent to the recipient. As with traditional bank transfers, the recipient does not see your crypto address or internal data.
“With Transaction Safety Levels, businesses can work with cryptocurrency without exposing sensitive operational data while remaining fully compatible with AML,” noted Vasily Zolochevsky, CBDO of BitHide. “This is how we build a bridge between essential privacy and AML requirements in the world of digital assets.”
Conclusion
In the reality of a transparent blockchain, businesses need not absolute anonymity but managed and regulated privacy. Companies must control the degree of data disclosure, protecting operational processes while maintaining AML compliance. This approach becomes the new realistic standard for corporate crypto technologies.
Basic privacy becomes an essential element of secure infrastructure, along with AML checks, data encryption, and robust wallet architecture. BitHide’s Transaction Safety Levels provide this control in practice: they hide sensitive metadata and prevent the construction and analysis of transaction graphs while remaining fully compliant.
BitHide does not offer an “anonymization” tool but rather a technology of controlled privacy that helps companies operate on the blockchain safely, legally, and without the risk of excessive data exposure. Contact our team to learn more about BitHide.


