Release 1.10: Implementation of BitHide via DarkWing

Release of DarkWing. Implementation of BitHide via DarkWing
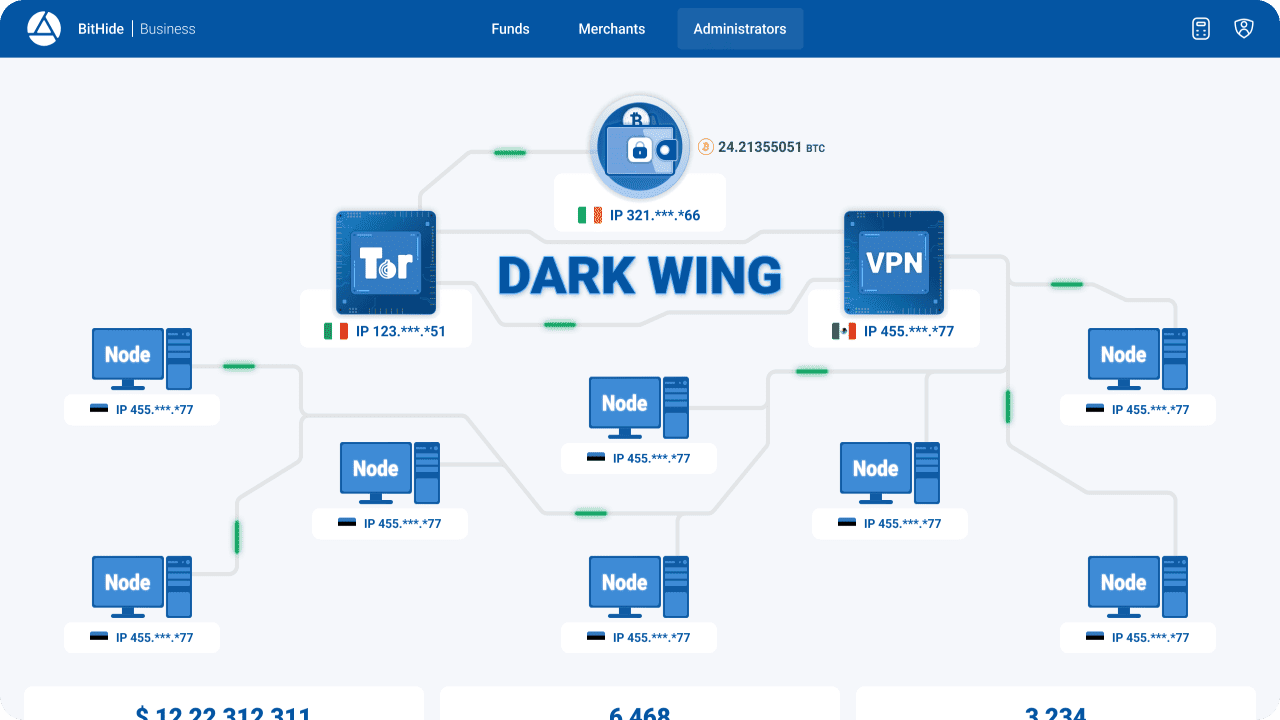
We are pleased to present the unique Dark Wing technology, integrated into BitHide, which ensures complete anonymity and security of crypto-payments for your business.
Dark Wing consists of two stages of hiding the user's real IP address. The first stage involves transmitting transaction data through the TOR network. In this network, data passes through a chain of three or more addresses, hiding the user's real IP address. However, most of the TOR IP addresses are blocked by the blockchain network, which is a disadvantage of this system. To overcome this problem, the second stage of Dark Wing technology involves the use of a VPN.
After passing through the TOR network, the user's transactions are transmitted to the servers of VPN service providers. Their IP addresses are no longer blocked by blockchain nodes, allowing users to freely use an anonymous gateway for crypto payments. With each new transaction, Dark Wing changes both the IP address for TOR and the IP address for VPN, which prevents transactions from being associated with the same wallet based on the IP address.
Dark Wing technology combines the advantages of TOR and VPN, eliminating their disadvantages. It provides anonymity and security when making crypto payments, allowing users to hide their real IP address and protect their financial transactions.